准备环境
一:把mybatis配置进来
(1): 在resources目下新增jdbc.properties配置文件,用于配置数据库的相关信息
jdbc.url = jdbc:mysql://IP地址:3306/ssm_security
jdbc.driverClass = com.mysql.jdbc.Driver
jdbc.username = 数据库用户名
jdbc.password = 数据库密码
(2): 修改applicationContext.xml文件
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:context="http://www.springframework.org/schema/context"
xmlns:aop="http://www.springframework.org/schema/aop" xmlns:tx="http://www.alibaba.com/schema/stat"
xsi:schemaLocation="http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans.xsd
http://www.springframework.org/schema/context
http://www.springframework.org/schema/context/spring-context.xsd
http://www.springframework.org/schema/aop
http://www.springframework.org/schema/aop/spring-aop.xsd http://www.alibaba.com/schema/stat http://www.alibaba.com/schema/stat.xsd">
<!—读取jdbc.properties –>
<context:property-placeholder location="classpath:jdbc.properties"/>
<!– 连接池 –>
<bean id="dataSource" class="com.alibaba.druid.pool.DruidDataSource">
<property name="url" value="${jdbc.url}"/>
<property name="driverClassName" value="${jdbc.driverClass}"/>
<property name="username" value="${jdbc.username}"/>
<property name="password" value="${jdbc.password}"/>
<property name="maxActive" value="10"/>
<property name="maxWait" value="3000"/>
</bean>
<!– mybatis整合Spring –>
<bean id="sqlSessionFactory" class="org.mybatis.spring.SqlSessionFactoryBean">
<property name="dataSource" ref="dataSource"/>
<!–别名扫描 –>
<property name="typeAliasesPackage" value="com.xhc.domain"/>
</bean>
<!–Mapper接口扫描 –>
<bean class="org.mybatis.spring.mapper.MapperScannerConfigurer">
<property name="basePackage" value="com.xhc.mapper"/>
</bean>
<!– 事务配置 –>
<bean id="transactionManager" class="org.springframework.jdbc.datasource.DataSourceTransactionManager">
<property name="dataSource" ref="dataSource"/>
</bean>
<context:component-scan base-package="com.xhc.service"/>
</beans>
新建配置文件中扫描的包,目前为止的package如下图
(3): resources下新增日志配置文件:log4j.properties
### direct log messages to stdout ###
log4j.appender.stdout=org.apache.log4j.ConsoleAppender
log4j.appender.stdout.Target=System.err
log4j.appender.stdout.layout=org.apache.log4j.PatternLayout
log4j.appender.stdout.layout.ConversionPattern=%d{ABSOLUTE} %5p %c{1}:%L – %m%n
### direct messages to file mylog.log ###
log4j.appender.file=org.apache.log4j.FileAppender
log4j.appender.file.File=c:mylog.log
log4j.appender.file.layout=org.apache.log4j.PatternLayout
log4j.appender.file.layout.ConversionPattern=%d{ABSOLUTE} %5p %c{1}:%L – %m%n
### set log levels – for more verbose logging change 'info' to 'debug' ###
log4j.rootLogger=debug, stdout
二:什么是RBAC
百度是这样解释的
RBAC(Role-based Access control),即基于角色的访问控制。首先RBAC不是一项技术,它是一个模型概念,一般用于系统权限的设计。
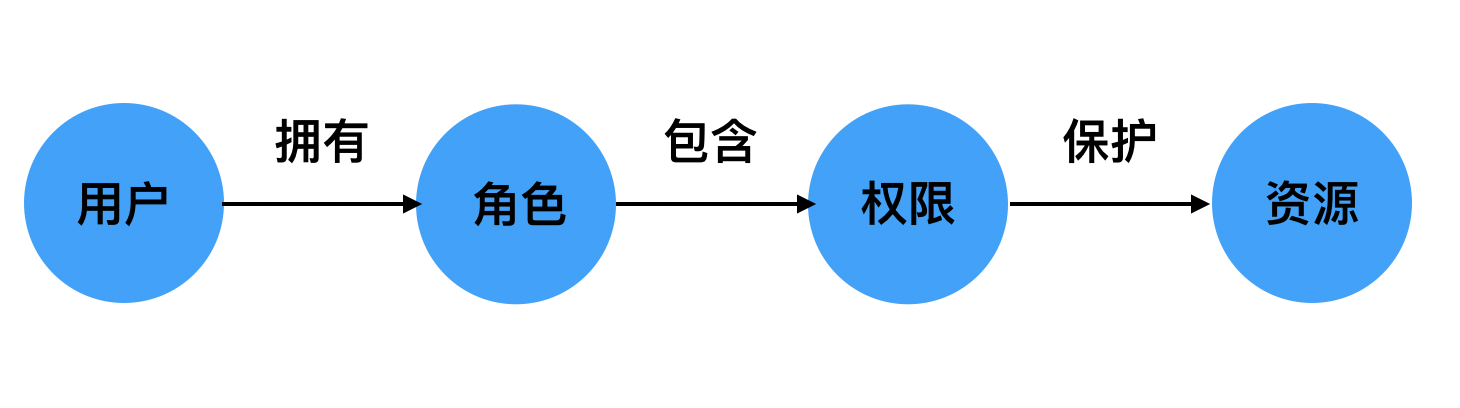
用户拥有什么角色,而这些角色又包含什么权限,这些权限保护着哪些资源。
在系统中,用户最终的目的是访问资源,但是出于安全考虑,用户不能直接访问资源。
RBAC设计的优势在于新增用户时,直接赋予角色就可以了,不需要和底层的权限资源打交道。而且一个角色可以赋予多个用户。
三:设计表并初始化数据
由RBAC模型可知,我们至少需要5张表。
- 用户表 sys_user
- 角色表 sys_role
- 权限表 sys_permission
- 用户角色关系表 sys_user_role
- 角色权限关系表 sys_role_permission
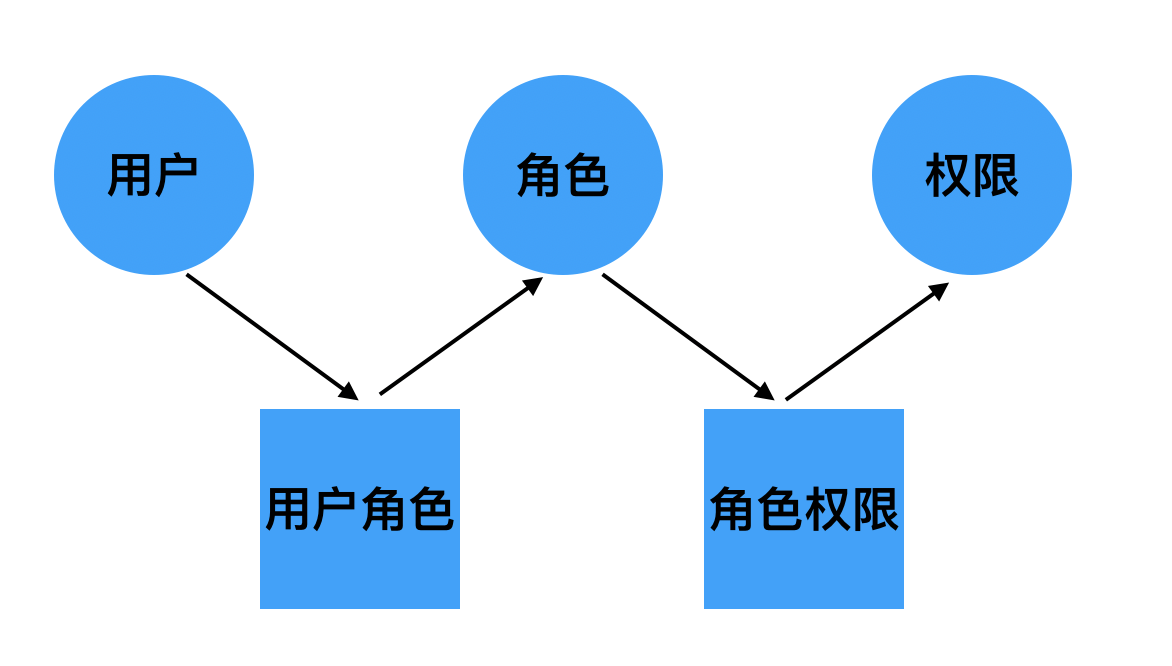
用户通过用户角色表找到对应的角色(一个用户可以有多个角色),然后角色通过角色权限表找到对应的权限。
建表和初始化的sql语句如下,直接复制运行或保存为.sql文件执行
SET NAMES utf8mb4;
SET FOREIGN_KEY_CHECKS = 0;
— Table structure for sys_permission
DROP TABLE IF EXISTS
sys_permission
;
CREATE TABLE
sys_permission
(
id
int(11) NOT NULL AUTO_INCREMENT COMMENT 'id',
permName
varchar(255) DEFAULT '' COMMENT '权限名称',
permTag
varchar(255) DEFAULT '' COMMENT '权限标记',
PRIMARY KEY (
id
)
) ENGINE=InnoDB AUTO_INCREMENT=5 DEFAULT CHARSET=utf8;
— Records of sys_permission
BEGIN;
INSERT INTO
sys_permission
VALUES (1, '商品显示', 'ROLE_LIST_GOODS');
INSERT INTO
sys_permission
VALUES (2, '商品添加', 'ROLE_ADD_GOODS');
INSERT INTO
sys_permission
VALUES (3, '商品删除', 'ROLE_DELETE_GOODS');
INSERT INTO
sys_permission
VALUES (4, '删除修改', 'ROLE_UPDATE_GOODS');
COMMIT;
— Table structure for sys_role
DROP TABLE IF EXISTS
sys_role
;
CREATE TABLE
sys_role
(
id
int(11) NOT NULL AUTO_INCREMENT COMMENT 'id',
roleName
varchar(255) DEFAULT '' COMMENT '角色名称',
roleDesc
varchar(255) DEFAULT '' COMMENT '角色描述',
PRIMARY KEY (
id
)
) ENGINE=InnoDB AUTO_INCREMENT=3 DEFAULT CHARSET=utf8;
— Records of sys_role
BEGIN;
INSERT INTO
sys_role
VALUES (1, '普通操作员', '普通操作员');
INSERT INTO
sys_role
VALUES (2, '高级操作员', '高级操作员');
COMMIT;
— Table structure for sys_role_permission
DROP TABLE IF EXISTS
sys_role_permission
;
CREATE TABLE
sys_role_permission
(
id
int(11) NOT NULL AUTO_INCREMENT COMMENT 'id',
role_id
int(11) DEFAULT NULL,
perm_id
int(11) DEFAULT NULL,
PRIMARY KEY (
id
)
) ENGINE=InnoDB AUTO_INCREMENT=5 DEFAULT CHARSET=utf8;
— Records of sys_role_permission
BEGIN;
INSERT INTO
sys_role_permission
VALUES (1, 1, 1);
INSERT INTO
sys_role_permission
VALUES (2, 1, 2);
INSERT INTO
sys_role_permission
VALUES (3, 2, 3);
INSERT INTO
sys_role_permission
VALUES (4, 2, 4);
COMMIT;
— Table structure for sys_user
DROP TABLE IF EXISTS
sys_user
;
CREATE TABLE
sys_user
(
id
int(11) NOT NULL AUTO_INCREMENT COMMENT 'id',
username
varchar(255) DEFAULT NULL COMMENT '用户名',
realname
varchar(255) DEFAULT NULL COMMENT '真实姓名',
password
varchar(255) DEFAULT NULL COMMENT '密码',
createDate
datetime DEFAULT NULL COMMENT '创建日期',
lastLoginTime
datetime DEFAULT NULL COMMENT '最后一次登录时间',
enabled
int(2) DEFAULT '1',
accountNonExpired
int(2) DEFAULT '1',
accountNonLocked
int(2) DEFAULT '1',
credentialsNonExpired
int(2) DEFAULT '1',
PRIMARY KEY (
id
)
) ENGINE=InnoDB AUTO_INCREMENT=3 DEFAULT CHARSET=utf8;
— Records of sys_user
BEGIN;
INSERT INTO
sys_user
VALUES (1, 'xhc1', '许洪昌', '123456', '2020-02-10 19:28:25', NULL, 1, 1, 1, 1);
INSERT INTO
sys_user
VALUES (2, 'xhc2', '小许', '123456', '2020-02-04 19:28:49', NULL, 1, 1, 1, 1);
COMMIT;
— Table structure for sys_user_role
DROP TABLE IF EXISTS
sys_user_role
;
CREATE TABLE
sys_user_role
(
id
int(11) NOT NULL AUTO_INCREMENT COMMENT 'id',
user_id
int(11) DEFAULT NULL,
role_id
int(11) DEFAULT NULL,
PRIMARY KEY (
id
)
) ENGINE=InnoDB AUTO_INCREMENT=3 DEFAULT CHARSET=utf8;
— Records of sys_user_role
BEGIN;
INSERT INTO
sys_user_role
VALUES (1, 1, 1);
INSERT INTO
sys_user_role
VALUES (2, 2, 2);
COMMIT;
SET FOREIGN_KEY_CHECKS = 1;
四:domain包下建立实体
package com.xhc.domain;
/**
* 权限
*/
public class Permission {
private Integer id;
private String permName;
private String permTag;
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getPermName() {
return permName;
}
public void setPermName(String permName) {
this.permName = permName;
}
public String getPermTag() {
return permTag;
}
public void setPermTag(String permTag) {
this.permTag = permTag;
}
}
package com.xhc.domain;
/**
* 角色
*/
public class Role {
private Integer id;
private String roleName;
private String roleDesc;
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getRoleName() {
return roleName;
}
public void setRoleName(String roleName) {
this.roleName = roleName;
}
public String getRoleDesc() {
return roleDesc;
}
public void setRoleDesc(String roleDesc) {
this.roleDesc = roleDesc;
}
}
package com.xhc.domain;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import java.util.ArrayList;
import java.util.Date;
import java.util.List;
/**
* 用户
*/
public class User implements UserDetails{
private Integer id;
private String username;
private String realname;
private String password;
private Date createDate;
private Date lastLoginTime;
private boolean enabled;
private boolean accountNonExpired;
private boolean accountNonLocked;
private boolean credentialsNonExpired;
//用户拥有的所有权限
private List<GrantedAuthority> authorities = new ArrayList<GrantedAuthority>();
public List<GrantedAuthority> getAuthorities() {
return authorities;
}
public void setAuthorities(List<GrantedAuthority> authorities) {
this.authorities = authorities;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
@Override
public String getUsername() {
return username;
}
public void setUsername(String username) {
this.username = username;
}
public String getRealname() {
return realname;
}
public void setRealname(String realname) {
this.realname = realname;
}
@Override
public String getPassword() {
return password;
}
public void setPassword(String password) {
this.password = password;
}
public Date getCreateDate() {
return createDate;
}
public void setCreateDate(Date createDate) {
this.createDate = createDate;
}
public Date getLastLoginTime() {
return lastLoginTime;
}
public void setLastLoginTime(Date lastLoginTime) {
this.lastLoginTime = lastLoginTime;
}
@Override
public boolean isEnabled() {
return enabled;
}
public void setEnabled(boolean enabled) {
this.enabled = enabled;
}
@Override
public boolean isAccountNonExpired() {
return accountNonExpired;
}
public void setAccountNonExpired(boolean accountNonExpired) {
this.accountNonExpired = accountNonExpired;
}
@Override
public boolean isAccountNonLocked() {
return accountNonLocked;
}
public void setAccountNonLocked(boolean accountNonLocked) {
this.accountNonLocked = accountNonLocked;
}
@Override
public boolean isCredentialsNonExpired() {
return credentialsNonExpired;
}
public void setCredentialsNonExpired(boolean credentialsNonExpired) {
this.credentialsNonExpired = credentialsNonExpired;
}
@Override
public String toString() {
return "User{" +
"id=" + id +
", username='" + username + ''' +
", realname='" + realname + ''' +
", password='" + password + ''' +
", createDate=" + createDate +
", lastLoginTime=" + lastLoginTime +
", enabled=" + enabled +
", accountNonExpired=" + accountNonExpired +
", accountNonLocked=" + accountNonLocked +
", credentialsNonExpired=" + credentialsNonExpired +
", authorities=" + authorities +
'}';
}
}
