Dashboard简介
在 Kubernetes 社区中,有一个很受欢迎的 Dashboard 项目,它可以给用户提供一个可视化的 Web 界面来查看当前集群的各种信息。用户可以用 Kubernetes Dashboard 部署容器化的应用、监控应用的状态、执行故障排查任务以及管理 Kubernetes 各种资源。
部署Dashboard
kubernetes集群准备
kubeadm部署3节点kubernetes1.13.0集群(master节点x1,node节点x2),集群部署参考:
https://www.daimajiaoliu.com/daima/476192d10900403
官方参考文档:
https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/\#deploying-the-dashboard-ui
github项目地址:
https://github.com/kubernetes/dashboard
这里部署dashboard v1.10.1版本。
由于yaml配置文件中指定镜像从google拉取,先下载yaml文件到本地,修改配置从阿里云仓库拉取镜像。
2
3
2
3
修改yaml配置文件image部分,指定镜像从阿里云镜像仓库拉取:
2
3
4
5
6
7
8
9
10
2......
3 containers:
4 - name: kubernetes-dashboard
5 #image: k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
6 image: registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
7 ports:
8......
9
10
然后执行以下命令部署dashboard服务:
2
3
4
5
6
7
8
9
10
2secret/kubernetes-dashboard-certs created
3serviceaccount/kubernetes-dashboard created
4role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
5rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
6deployment.apps/kubernetes-dashboard created
7service/kubernetes-dashboard created
8[centos@k8s-master ~]$
9
10
查看Pod 的状态为running说明dashboard已经部署成功:
2
3
4
5
2kubernetes-dashboard-847f8cb7b8-wrm4l 1/1 Running 0 19m 10.244.2.5 k8s-node2 <none> <none>
3[centos@k8s-master ~]$
4
5
Dashboard 会在 kube-system namespace 中创建自己的 Deployment 和 Service:
2
3
4
5
6
7
8
9
10
2NAME READY UP-TO-DATE AVAILABLE AGE
3kubernetes-dashboard 1/1 1 1 21m
4[centos@k8s-master ~]$
5[centos@k8s-master ~]$ kubectl get service kubernetes-dashboard --namespace=kube-system
6NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
7kubernetes-dashboard ClusterIP 10.104.254.251 <none> 443/TCP 21m
8[centos@k8s-master ~]$
9
10
访问dashboard
有以下几种方式访问dashboard:
- Nodport方式访问dashboard,service类型改为NodePort
- loadbalacer方式,service类型改为loadbalacer
- Ingress方式访问dashboard
- API server方式访问 dashboard
- kubectl proxy方式访问dashboard
NodePort方式
为了便于本地访问,修改yaml文件,将service改为NodePort 类型:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
2......
3---
4# ------------------- Dashboard Service ------------------- #
5
6kind: Service
7apiVersion: v1
8metadata:
9 labels:
10 k8s-app: kubernetes-dashboard
11 name: kubernetes-dashboard
12 namespace: kube-system
13spec:
14 type: NodePort #增加type: NodePort
15 ports:
16 - port: 443
17 targetPort: 8443
18 nodePort: 31620 #增加nodePort: 31620
19 selector:
20 k8s-app: kubernetes-dashboard
21
22
重新应用yaml文件
2
3
2
3
查看service,TYPE类型已经变为NodePort,端口为31620
2
3
4
5
2kubernetes-dashboard NodePort 10.107.160.197 <none> 443:31620/TCP 32m
3[centos@k8s-master ~]$
4
5
通过浏览器访问:https://192.168.92.56:31620/, 登录界面如下:
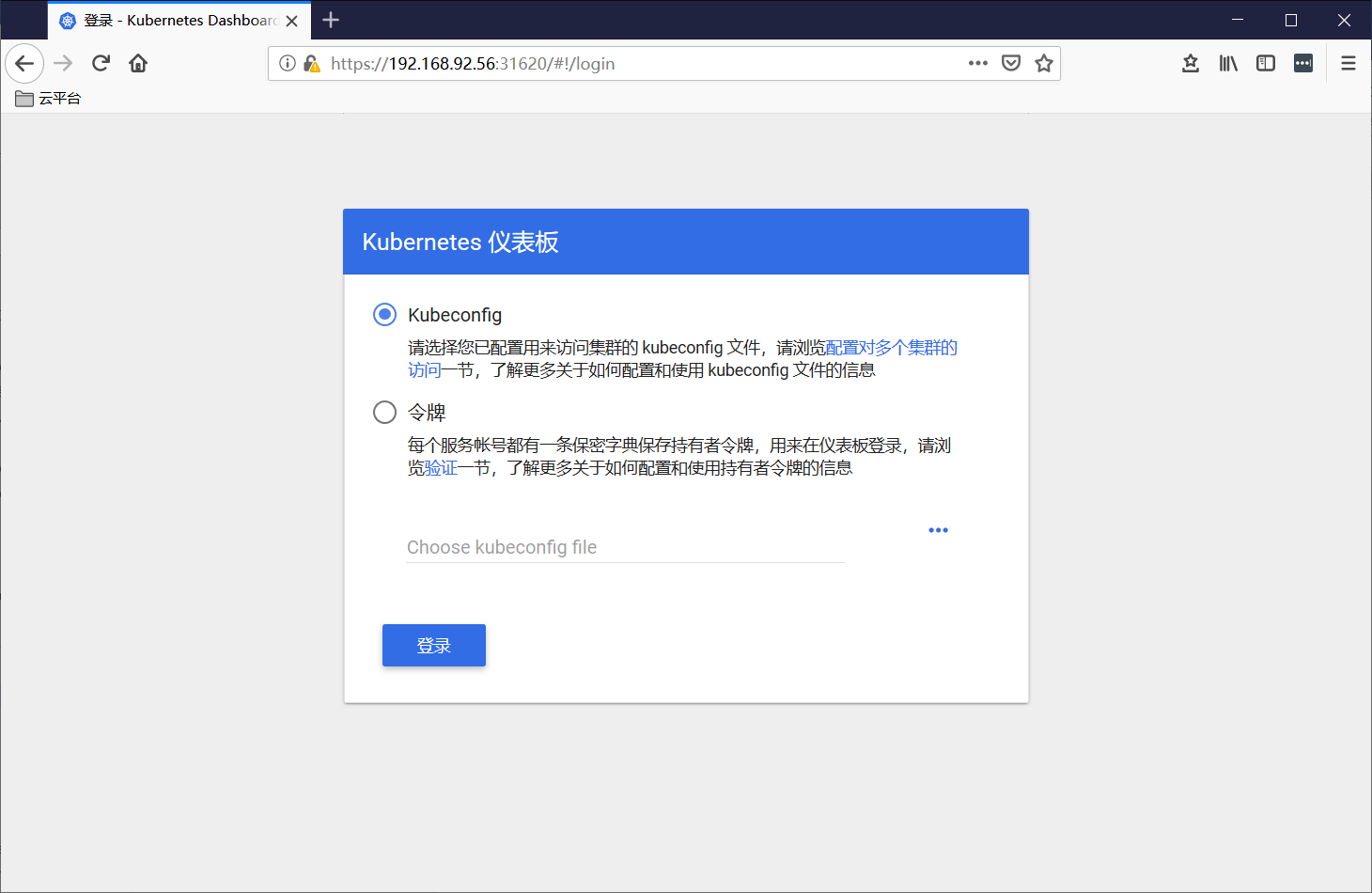
Dashboard 支持 Kubeconfig 和 Token 两种认证方式,我们这里选择Token认证方式登录:
创建登录用户
官方参考文档:
https://github.com/kubernetes/dashboard/wiki/Creating-sample-user
创建dashboard-adminuser.yaml:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
2apiVersion: v1
3kind: ServiceAccount
4metadata:
5 name: admin-user
6 namespace: kube-system
7---
8apiVersion: rbac.authorization.k8s.io/v1
9kind: ClusterRoleBinding
10metadata:
11 name: admin-user
12roleRef:
13 apiGroup: rbac.authorization.k8s.io
14 kind: ClusterRole
15 name: cluster-admin
16subjects:
17- kind: ServiceAccount
18 name: admin-user
19 namespace: kube-system
20
21
执行yaml文件:
2
3
2
3
说明:上面创建了一个叫admin-user的服务账号,并放在kube-system命名空间下,并将cluster-admin角色绑定到admin-user账户,这样admin-user账户就有了管理员的权限。默认情况下,kubeadm创建集群时已经创建了cluster-admin角色,我们直接绑定即可。
查看admin-user账户的token
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
2Name: admin-user-token-jtlbp
3Namespace: kube-system
4Labels: <none>
5Annotations: kubernetes.io/service-account.name: admin-user
6 kubernetes.io/service-account.uid: a345b4d5-1006-11e9-b90d-000c291c25f3
7
8Type: kubernetes.io/service-account-token
9
10Data
11====
12ca.crt: 1025 bytes
13namespace: 11 bytes
14token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLWp0bGJwIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiJhMzQ1YjRkNS0xMDA2LTExZTktYjkwZC0wMDBjMjkxYzI1ZjMiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZS1zeXN0ZW06YWRtaW4tdXNlciJ9.uv3pzkM3_WQ8_gOwzEvKGrwfhXKtQmDYtfMpjmCDsPsq7OP3W5o0uFxKS7q2zbxw_pFZ3pFMyEk462RZo5z-Z6AB9gOXffvhqllSIQi3SzesvRcBqqW1n48SalGgBkCiqkX4DjjYDrHCAd5m-Uc7e3N28jWW5O4gUXEWwUtcobLVflEOnZ9Ykx9JBZPkmmS25toyoE6v8W7Zuv1moGBxmx4_AEnAFBUNDjZ7AxvmERQL-cQk6vsfrQ-hPejE1L3kgLbhpQnqQ3lJ3z7hrGMur31muW3WeOvd3Aciqr0TliyP1Wllf-hPuLPDsLdNZJpMx1B8O5jnw1cYbLsqQAaUXQ
15[centos@k8s-master ~]$
16
17
把获取到的Token复制到登录界面的Token输入框中:
成功登陆dashboard:

loadbalacer方式
首先需要部署metallb负载均衡器,部署参考:
https://www.daimajiaoliu.com/daima/4edbc6cd9900400
修改kubernetes-dashboard.yaml文件,最后service部分改为type: LoadBalancer即可:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
2......
3---
4# ------------------- Dashboard Service ------------------- #
5
6kind: Service
7apiVersion: v1
8metadata:
9 labels:
10 k8s-app: kubernetes-dashboard
11 name: kubernetes-dashboard
12 namespace: kube-system
13spec:
14 type: LoadBalancer
15 ports:
16 - port: 443
17 targetPort: 8443
18 selector:
19 k8s-app: kubernetes-dashboard
20
21
重新应用yaml文件
2
3
2
3
注意由nodeport改为其他类型需要添加–forece才能执行成功。
查看service,TYPE类型已经变为LoadBalancer,并且分配了EXTERNAL-IP:
2
3
4
5
6
2NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
3kubernetes-dashboard LoadBalancer 10.107.160.197 192.168.92.202 443:32471/TCP 10m
4[centos@k8s-master ~]$
5
6
浏览器输入https://192.168.92.202访问,填写之前申请的token进行登录:
登录成功:
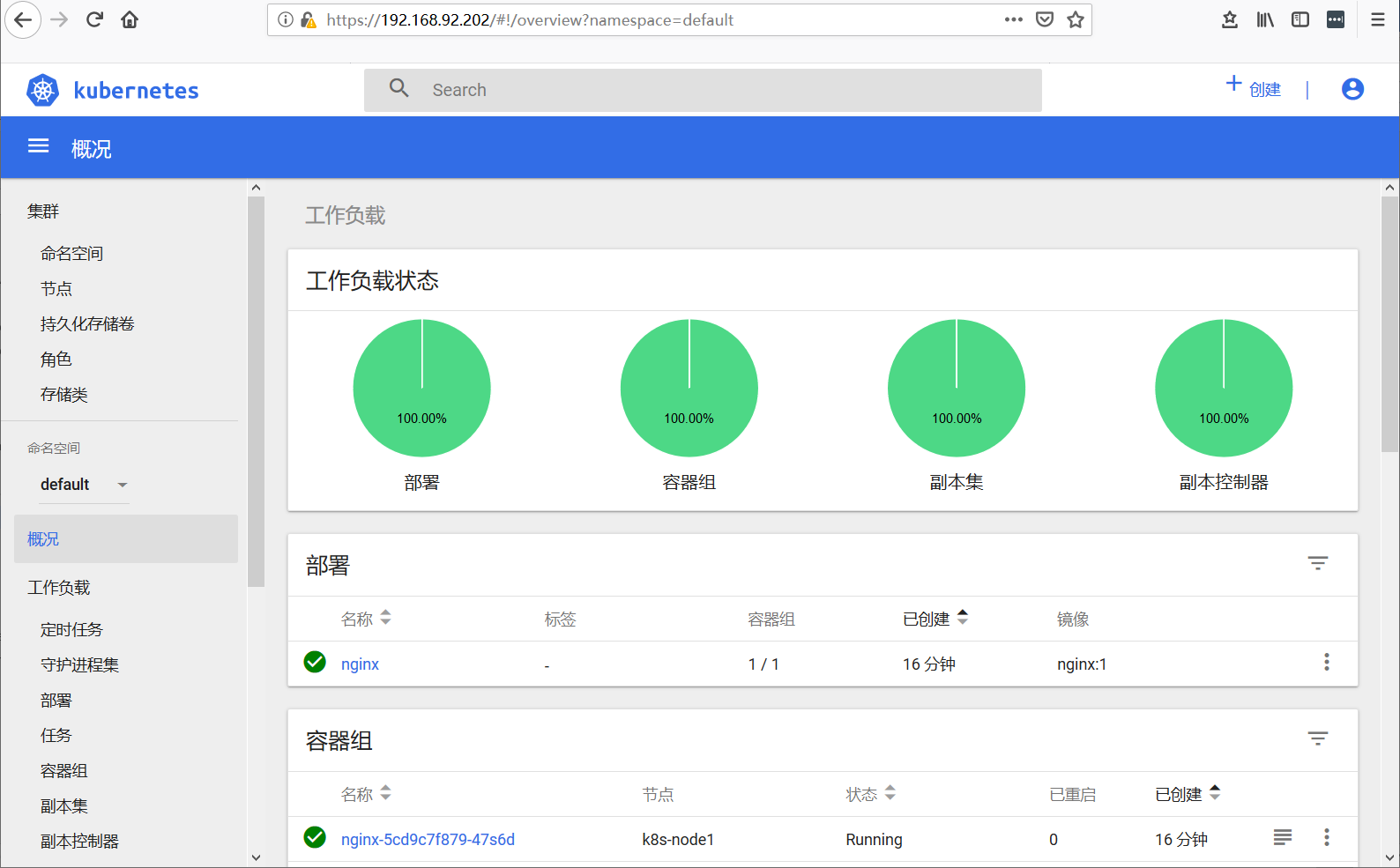
nginx-ingress方式
部署nginx-ingress-controller
2
3
4
2$ kubectl apply -f mandatory.yaml
3
4
详细部署参考:https://www.daimajiaoliu.com/daima/4796bd6f2900408
创建Dashboard TLS证书
2
3
4
5
6
7
8
9
10
2$ cd /usr/local/src/kubernetes
3$ openssl genrsa -des3 -passout pass:x -out certs/dashboard.pass.key 2048
4$ openssl rsa -passin pass:x -in certs/dashboard.pass.key -out certs/dashboard.key
5$ openssl req -new -key certs/dashboard.key -out certs/dashboard.csr -subj '/CN=kube-dashboard'
6$ openssl x509 -req -sha256 -days 365 -in certs/dashboard.csr -signkey certs/dashboard.key -out certs/dashboard.crt
7$ rm certs/dashboard.pass.key
8$ kubectl create secret generic kubernetes-dashboard-certs --from-file=certs -n kube-system
9
10
创建ingress规则
文件末尾添加tls配置项即可。
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
2apiVersion: extensions/v1beta1
3kind: Ingress
4metadata:
5 labels:
6 k8s-app: kubernetes-dashboard
7 annotations:
8 kubernetes.io/ingress.class: "nginx"
9 # https://github.com/kubernetes/ingress-nginx/blob/master/docs/user-guide/nginx-configuration/annotations.md
10 nginx.ingress.kubernetes.io/ssl-redirect: "true"
11 nginx.ingress.kubernetes.io/ssl-passthrough: "true"
12 name: kubernetes-dashboard
13 namespace: kube-system
14spec:
15 rules:
16 - host: dashboard.host.com
17 http:
18 paths:
19 - path: /
20 backend:
21 servicePort: 443
22 serviceName: kubernetes-dashboard
23 tls:
24 - hosts:
25 - dashboard.host.com
26 secretName: kubernetes-dashboard-certs
27
28
查看创建的ingress:
2
3
4
5
6
2NAME HOSTS ADDRESS PORTS AGE
3kubernetes-dashboard dashboard.host.com 80, 443 30h
4[centos@k8s-master ~]$
5
6
暴露nginx-ingress-controller服务
要想暴露内部流量,需要让 Ingress Controller 自身能够对外提供服务,主要有以下几种方式:
hostport
nodeport
loadbalacer
hostport方式
修改nginx-ingress-controller yaml配置文件,将Ingress Controller 改为 DeamonSet 方式部署(注释replicas),在每个节点运行一个nginx-ingress-controller的pod,然后在containers.ports部分做主机端口映射,添加 hostPort: 80和 hostPort: 443
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
2......
3---
4
5apiVersion: extensions/v1beta1
6kind: DaemonSet #改为DaemonSet
7metadata:
8 name: nginx-ingress-controller
9 namespace: ingress-nginx
10 labels:
11 app.kubernetes.io/name: ingress-nginx
12 app.kubernetes.io/part-of: ingress-nginx
13spec:
14# replicas: 1 #注释掉replicas
15......
16 ports:
17 - name: http
18 containerPort: 80
19 hostPort: 80
20 - name: https
21 containerPort: 443
22 hostPort: 443
23......
24
25
更新yaml配置文件:
2
3
2
3
查看运行的pod:
2
3
4
5
6
7
8
2NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
3nginx-ingress-controller-bhccq 1/1 Running 0 18s 10.244.2.102 k8s-node2 <none> <none>
4nginx-ingress-controller-fssbt 1/1 Running 0 18s 10.244.0.55 k8s-master <none> <none>
5nginx-ingress-controller-z7xsf 1/1 Running 0 18s 10.244.1.101 k8s-node1 <none> <none>
6[centos@k8s-master ~]$
7
8
修改dashboard yaml文件配置
在deployment.containers部分增加args配置,在service部分改回默认即可:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
2......
3---
4# ------------------- Dashboard Deployment ------------------- #
5
6kind: Deployment
7apiVersion: apps/v1beta2
8metadata:
9 labels:
10 k8s-app: kubernetes-dashboard
11 name: kubernetes-dashboard
12 namespace: kube-system
13spec:
14 replicas: 1
15 revisionHistoryLimit: 10
16 selector:
17 matchLabels:
18 k8s-app: kubernetes-dashboard
19 template:
20 metadata:
21 labels:
22 k8s-app: kubernetes-dashboard
23 spec:
24 containers:
25 - name: kubernetes-dashboard
26 #image: k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
27 image: registry.cn-hangzhou.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
28 ports:
29 - containerPort: 8443
30 protocol: TCP
31 args:
32 - --tls-key-file=dashboard.key
33 - --tls-cert-file=dashboard.crt
34 #- --auto-generate-certificates
35 # Uncomment the following line to manually specify Kubernetes API server Host
36 # If not specified, Dashboard will attempt to auto discover the API server and connect
37 # to it. Uncomment only if the default does not work.
38 # - --apiserver-host=http://my-address:port
39 volumeMounts:
40......
41---
42# ------------------- Dashboard Service ------------------- #
43
44kind: Service
45apiVersion: v1
46metadata:
47 labels:
48 k8s-app: kubernetes-dashboard
49 name: kubernetes-dashboard
50 namespace: kube-system
51spec:
52 ports:
53 - port: 443
54 targetPort: 8443
55 selector:
56 k8s-app: kubernetes-dashboard
57
58
最后应用变更:
2
3
2
3
查看dashboard service:
2
3
4
5
6
7
2NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
3......
4kubernetes-dashboard ClusterIP 10.96.55.60 <none> 443/TCP 30h
5[centos@k8s-master ~]$
6
7
集群外部节点配置DNS解析:
2
3
4
5
2192.168.92.57 dashboard.host.com
3192.168.92.58 dashboard.host.com
4
5
集群外部直接访问:https://dashboard.host.com
填入之前申请的token,访问成功:
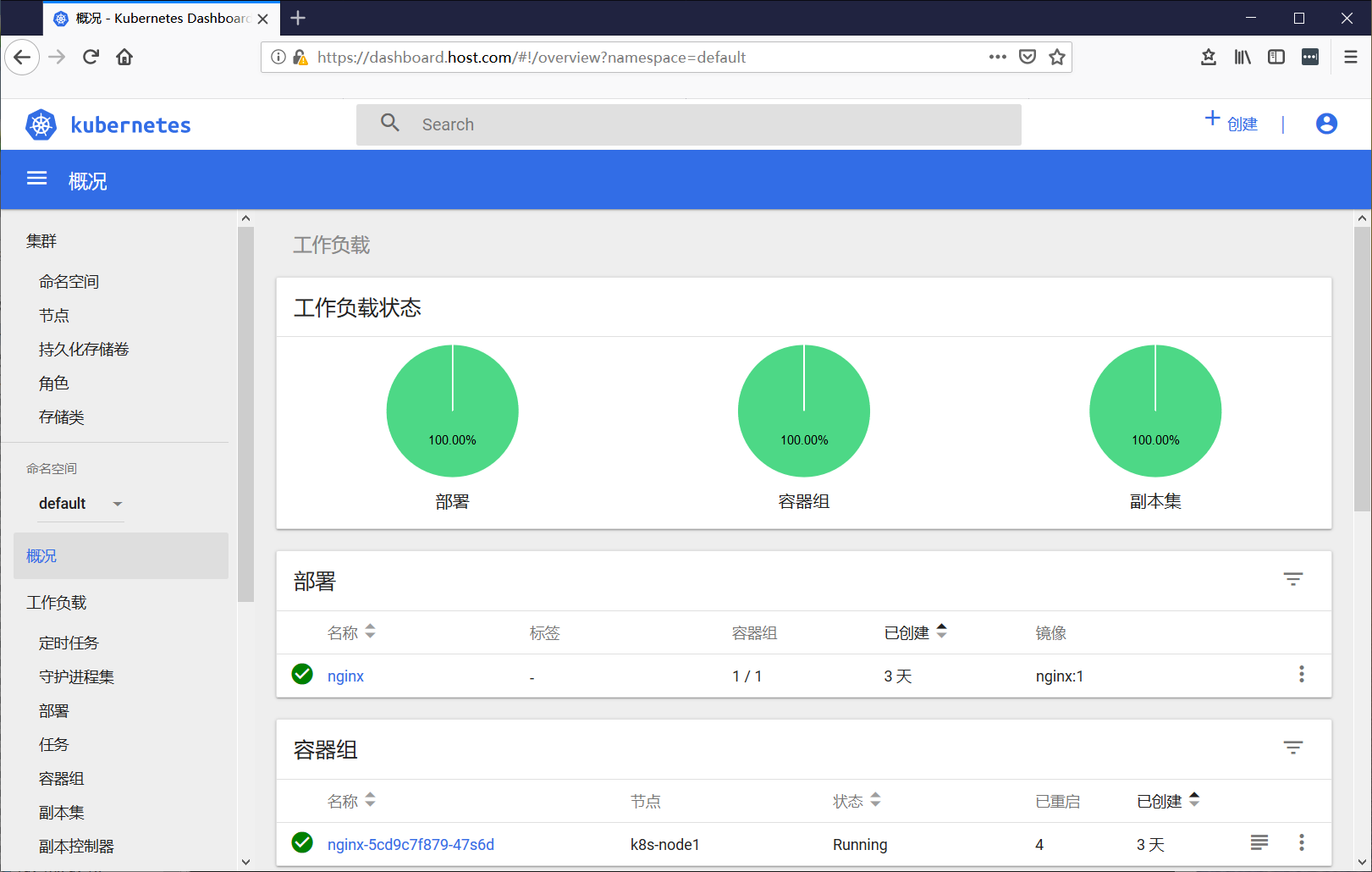
NodePort方式
修改nginx-ingress-controller配置文件mandatory.yaml,删除containers.ports部分做的主机端口映射,hostPort: 80和 hostPort: 443
并为nginx-ingress-controller创建NodePort类型的service,通过nodeip+port方式对外提供服务:
2
3
4
2$ kubectl apply -f service-nodeport.yaml
3
4
直接执行yaml文件即可,可以看到创建了nginx-ingress-controller的NodePort类型service:
2
3
4
5
6
2NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
3ingress-nginx NodePort 10.100.30.8 <none> 80:32142/TCP,443:32179/TCP 29h
4[centos@k8s-master ~]$
5
6
集群外主机hosts配置文件不变
2
3
4
5
2192.168.92.57 dashboard.host.com
3192.168.92.58 dashboard.host.com
4
5
选择token方式,通过域名+port方式访问:https://dashboard.host.com:32179
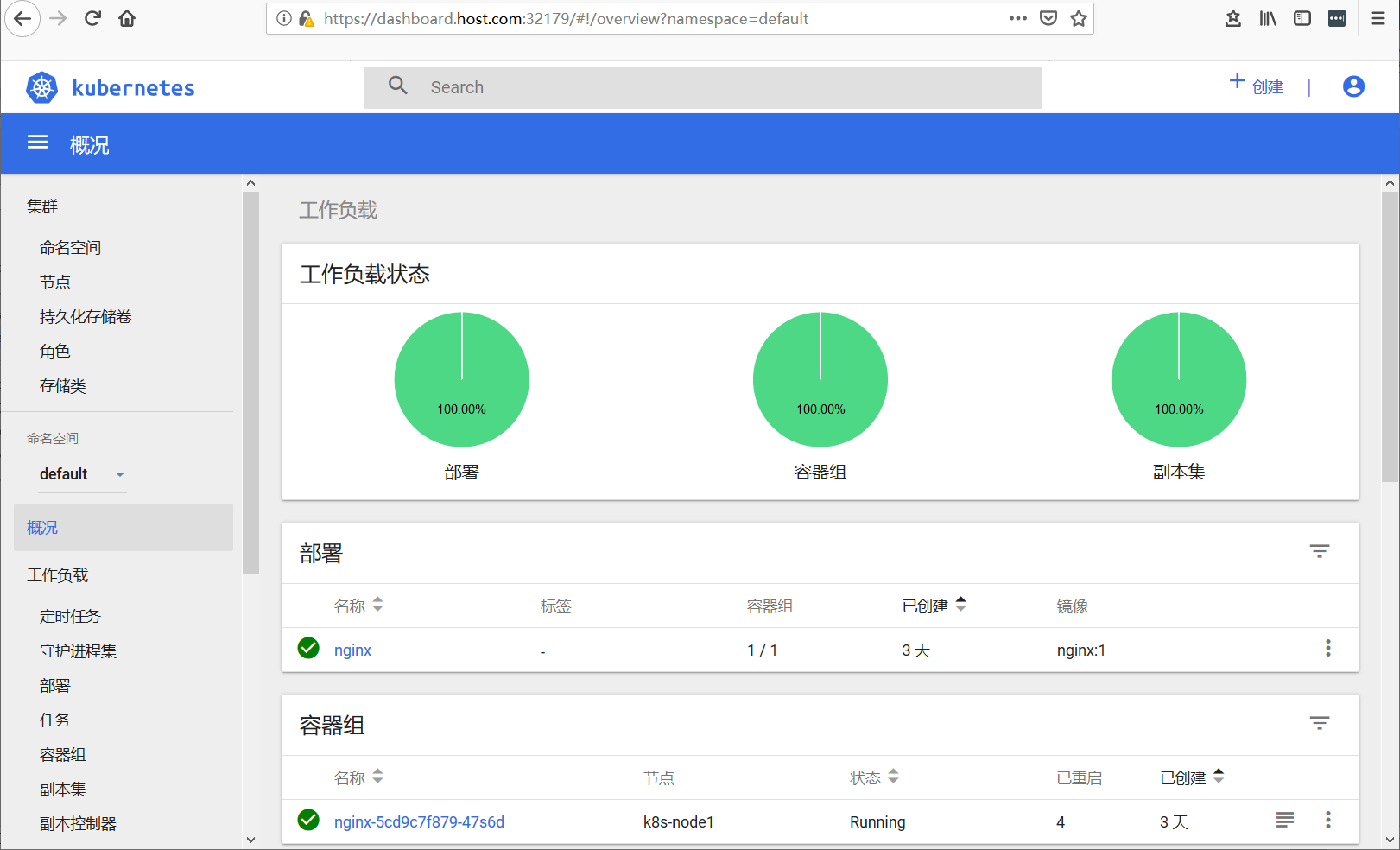
loadbalancer方式
首先需要部署loadbalancer,参考这里:
https://www.daimajiaoliu.com/daima/4edbc6cd9900400
然后修改nginx ingress controller的service类型为type: LoadBalancer即可:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
2apiVersion: v1
3kind: Service
4metadata:
5 name: ingress-nginx
6 namespace: ingress-nginx
7 labels:
8 app.kubernetes.io/name: ingress-nginx
9 app.kubernetes.io/part-of: ingress-nginx
10spec:
11 type: LoadBalancer
12 ports:
13 - name: http
14 port: 80
15 targetPort: 80
16 protocol: TCP
17 - name: https
18 port: 443
19 targetPort: 443
20 protocol: TCP
21 selector:
22 app.kubernetes.io/name: ingress-nginx
23 app.kubernetes.io/part-of: ingress-nginx
24
25
更新yaml文件:
2
3
2
3
查看service 类型以及获取到的EXTERNAL-IP
2
3
4
5
6
2NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
3ingress-nginx LoadBalancer 10.111.158.158 192.168.92.200 80:32629/TCP,443:30118/TCP 20s
4[centos@k8s-master ~]$
5
6
修改集群外主机hosts配置文件,配置下面一条即可
2
3
2
3
通过token方式浏览器访问:https://dashboard.host.com
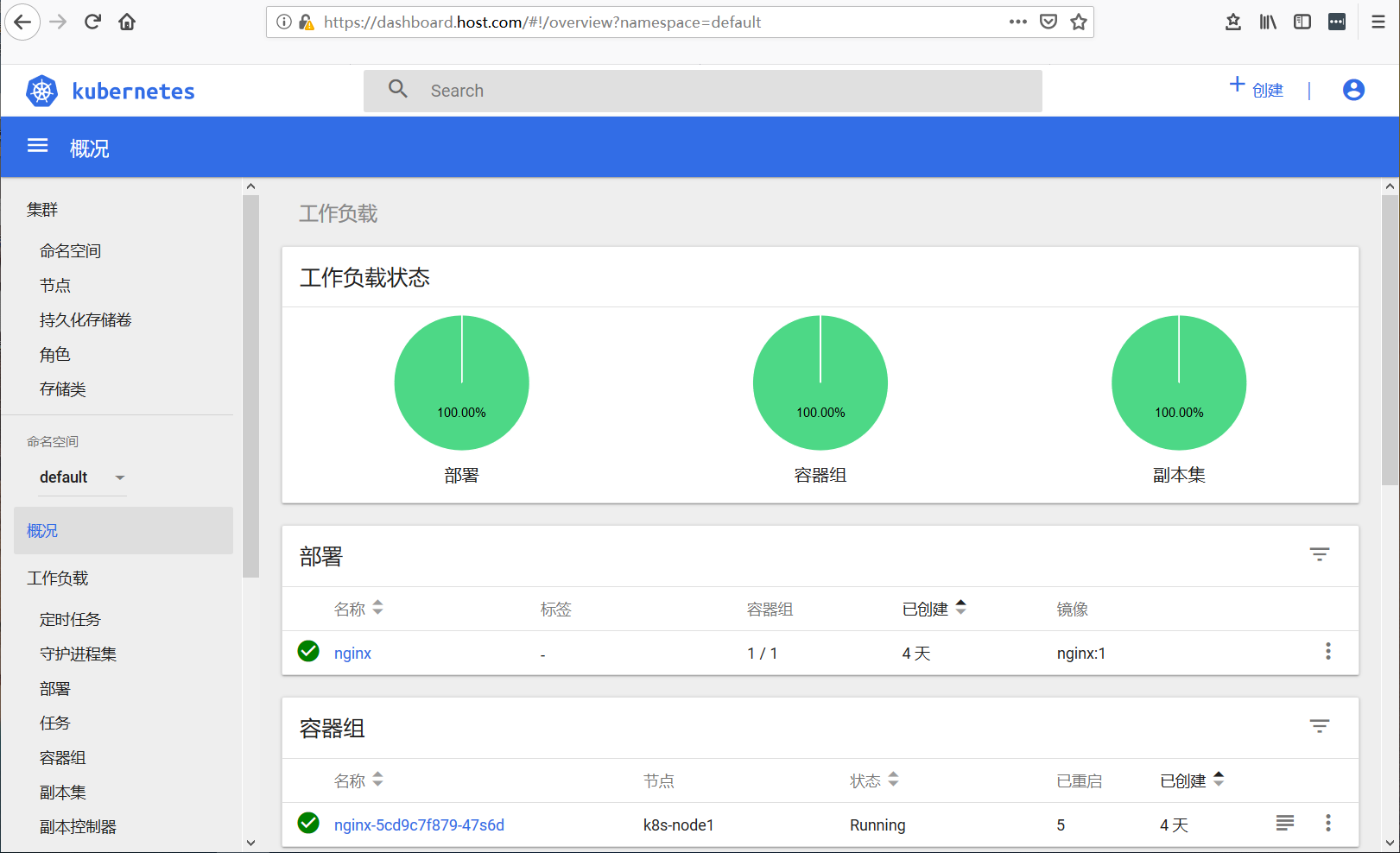
API Server方式
如果Kubernetes API服务器是公开的,并可以从外部访问,那我们可以直接使用API Server的方式来访问,也是比较推荐的方式。
Dashboard的访问地址为:
2
3
2
3
但是浏览器返回的结果可能如下:
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
2 "kind": "Status",
3 "apiVersion": "v1",
4 "metadata": {
5
6 },
7 "status": "Failure",
8 "message": "services \"https:kubernetes-dashboard:\" is forbidden: User \"system:anonymous\" cannot get resource \"services/proxy\" in API group \"\" in the namespace \"kube-system\"",
9 "reason": "Forbidden",
10 "details": {
11 "name": "https:kubernetes-dashboard:",
12 "kind": "services"
13 },
14 "code": 403
15}
16
17
这是因为最新版的k8s默认启用了RBAC,并为未认证用户赋予了一个默认的身份:anonymous。
对于API Server来说,它是使用证书进行认证的,我们需要先创建一个证书:
我们使用client-certificate-data和client-key-data生成一个p12文件,可使用下列命令:
2
3
4
5
6
7
8
9
10
11
12
2grep 'client-certificate-data' ~/.kube/config | head -n 1 | awk '{print $2}' | base64 -d >> kubecfg.crt
3# 生成client-key-data
4grep 'client-key-data' ~/.kube/config | head -n 1 | awk '{print $2}' | base64 -d >> kubecfg.key
5# 生成p12
6openssl pkcs12 -export -clcerts -inkey kubecfg.key -in kubecfg.crt -out kubecfg.p12 -name "kubernetes-client"
7[centos@k8s-master ~]$ ll
8-rw-rw-r-- 1 centos centos 1082 Dec 28 19:41 kubecfg.crt
9-rw-rw-r-- 1 centos centos 1675 Dec 28 19:41 kubecfg.key
10-rw-rw-r-- 1 centos centos 2464 Dec 28 19:41 kubecfg.p12
11
12
最后导入上面生成的p12文件,重新打开浏览器,显示如下:
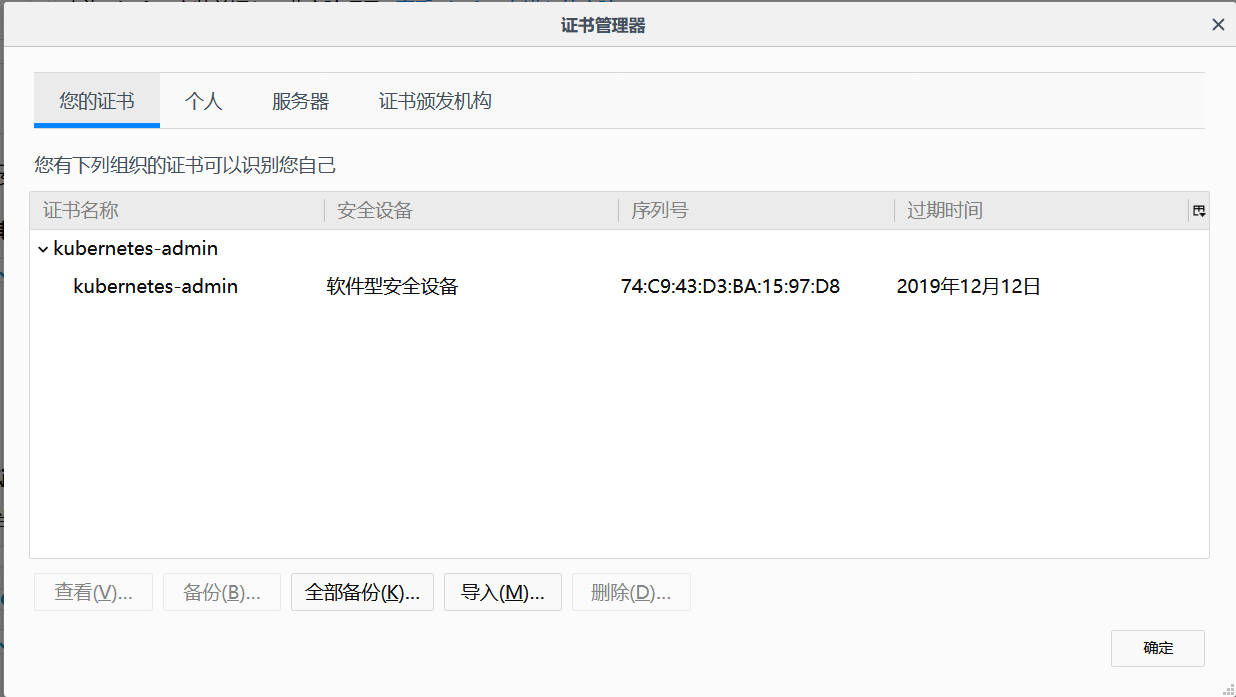
点击确定,便可以看到熟悉的登录界面了:
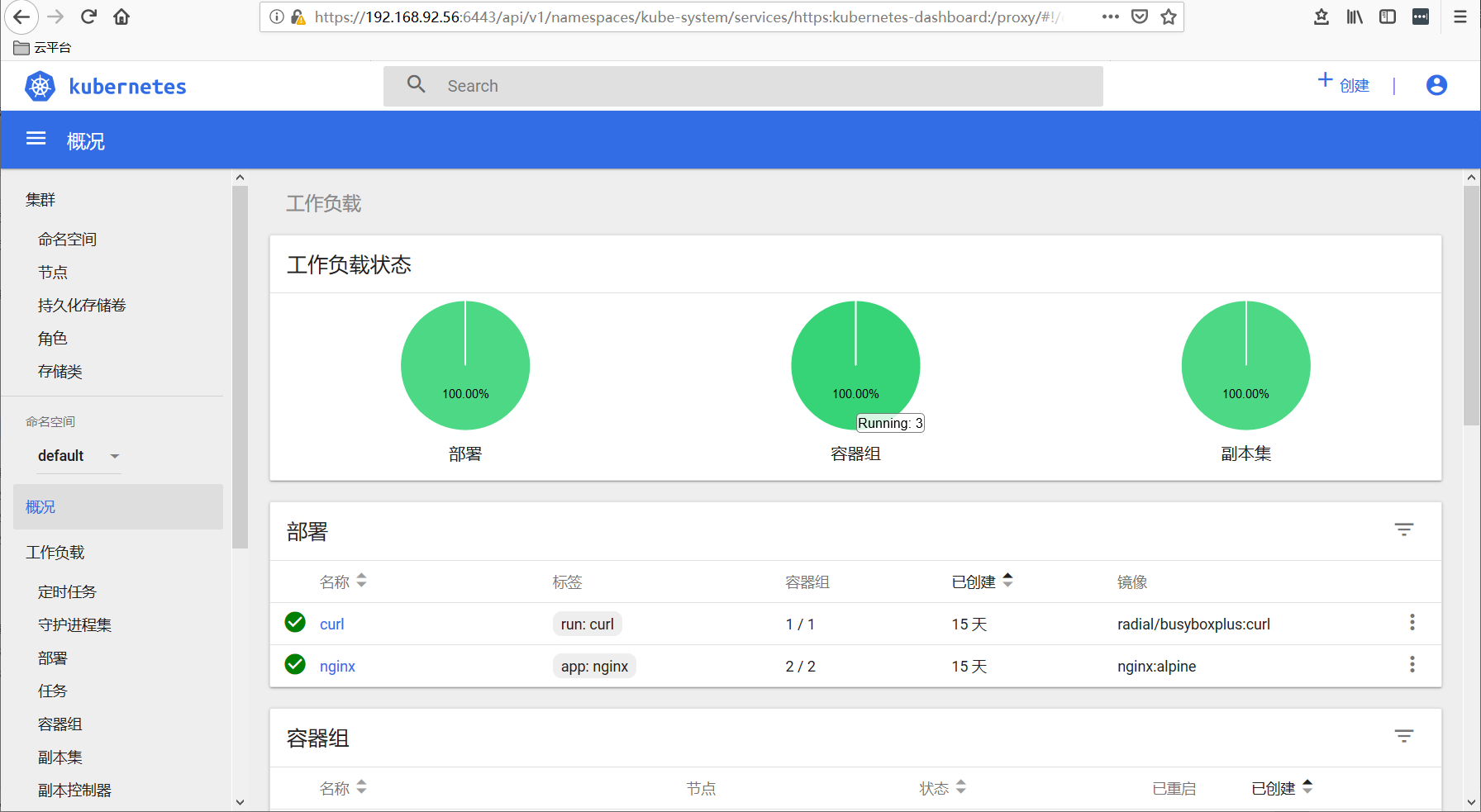
我们可以使用一开始创建的admin-user用户的token进行登录,一切OK。
https://192.168.92.56:6443/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/
Porxy方式
如果要在本地访问dashboard,可运行如下命令:
2
3
4
2Starting to serve on 127.0.0.1:8001
3
4
现在就可以通过以下链接来访问Dashborad UI
2
3
2
3
这种方式默认情况下,只能从本地访问(启动它的机器)。
我们也可以使用–address和–accept-hosts参数来允许外部访问:
2
3
4
2Starting to serve on [::]:8001
3
4
然后我们在外网访问以下链接:
2
3
2
3
可以成功访问到登录界面,但是填入token也无法登录,这是因为Dashboard只允许localhost和127.0.0.1使用HTTP连接进行访问,而其它地址只允许使用HTTPS。因此,如果需要在非本机访问Dashboard的话,只能选择其他访问方式。
使用Dashboard
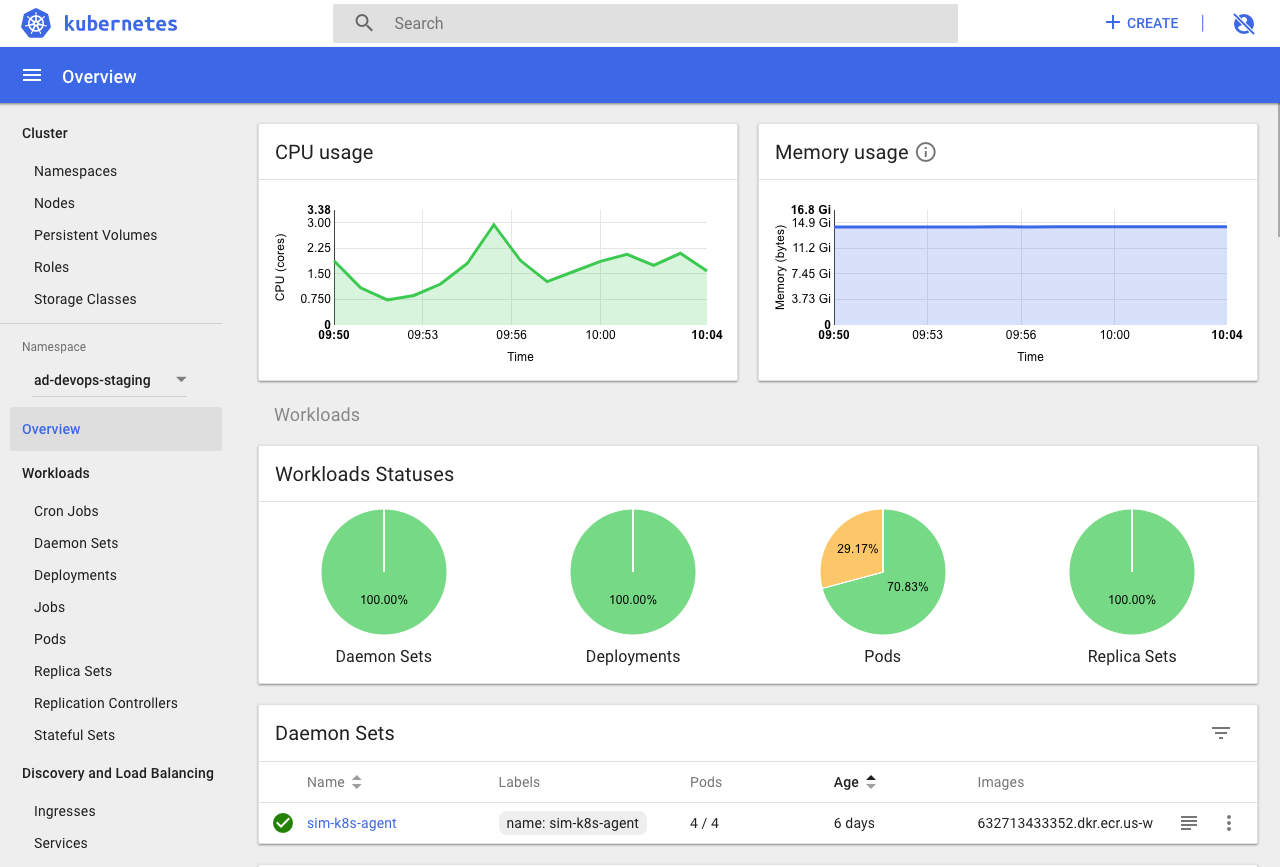
Dashboard 界面结构分为三个大的区域。
- 顶部操作区,在这里用户可以搜索集群中的资源、创建资源或退出。
- 左边导航菜单,通过导航菜单可以查看和管理集群中的各种资源。菜单项按照资源的层级分为两类:Cluster 级别的资源 ,Namespace 级别的资源 ,默认显示的是 default Namespace,可以进行切换:
- 中间主体区,在导航菜单中点击了某类资源,中间主体区就会显示该资源所有实例,比如点击 Pods。
