- 超文本传输协议http协议被用于在Web浏览器和网站服务器之间传递信息,http协议以明文方式发送内容,不提供任何方式的数据加密,安全性低。
- 安全套接字层超文本传输协议https,基于HTTP协议,通过SSL或TLS提供加密处理数据、验证对方身份以及数据完整性保护。
- https协议需要到CA申请证书,阿里云也提供了相应的服务,今天我们就手工生成证书来测试,当然浏览器通过https访问,会提示“不安全”,因为这个证书不是CA系统签发的,以后有项目需求,可以去阿里云购买SLL证书。
1、生成CA证书
(1)查看openssl是否安装
2
3
2
3
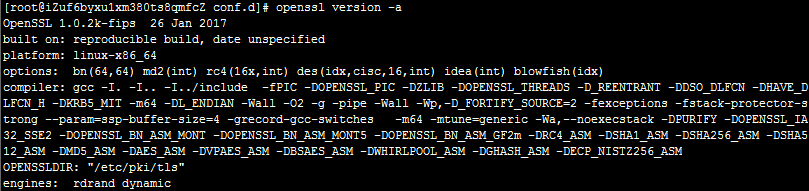
- OPENSSLDIR: “/etc/pki/tls”,这个是openssl的安装位置
(2)搭建ca服务器:
-
根据配置文件信息,到CA根目录,若没有则自己创建
2
3
4
5
2mkdir -pv {certs,crl,newcerts,private}
3touch {serial,index.txt}
4
5
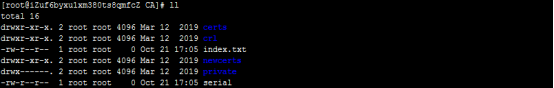
-
证书开始编号
2
3
2
3
-
ca生成自己的私钥
2
3
2
3
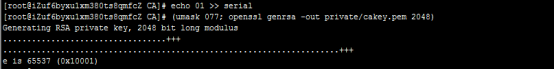
-
生成自签证书
2
3
2
3
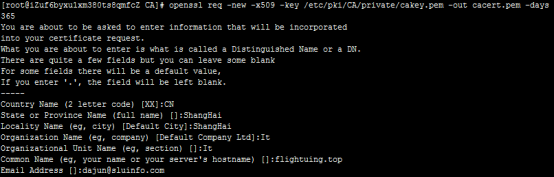
(3)颁发证书
-
CA搭好了,我们就可以使用这个来为其他证书签名。
-
生成私钥(位置随意)
2
3
2
3
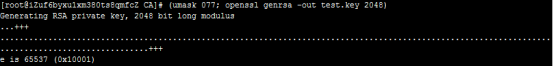
-
生成证书签署请求
2
3
2
3
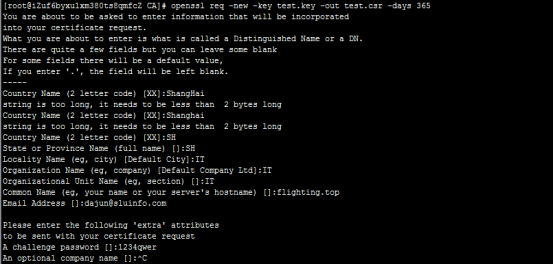
- 此处的CountryName、State、Locality Name、Organization Name、Organizational Unit Name必须和根证书CA的相同,这点注意一下。
(4)在CA服务器上签署证书
-
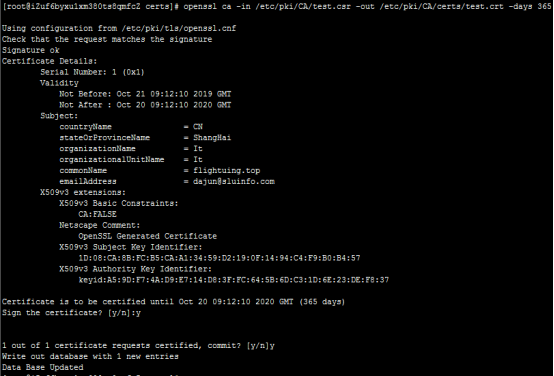
将3生成的.csr文件传输给ca服务器,ca服务器使用命令签署该证,当然我们测试,都在同一个服务器上,直接就在当前目录下操作了。
2
3
4
2openssl ca -in /etc/pki/CA/test.csr -out /etc/pki/CA/certs/test.crt -days 365
3
4
2
3
4
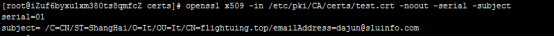
2openssl x509 -in /etc/pki/CA/test.crt -noout -serial -subject
3
4
-
如何将.crt的ssl证书文件转换成.pem格式
2
3
2
3
2、配置Nginx的证书
-
上面已经生成了CA证书
-
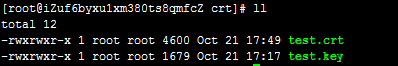
在nginx目录下新建crt目录,把生成的test.crt、test.key移动过去
2
3
4
2mkdir crt
3
4
-
下面的比较重要,修改ngxin.conf
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
2user nginx;
3pid /var/run/nginx.pid;
4worker_processes auto;
5worker_rlimit_nofile 65535;
6
7events {
8 multi_accept on;
9 worker_connections 65535;
10}
11
12http {
13 charset utf-8;
14 sendfile on;
15 tcp_nopush on;
16 tcp_nodelay on;
17 server_tokens off;
18 log_not_found off;
19 types_hash_max_size 2048;
20 client_max_body_size 16M;
21
22 # MIME
23 include mime.types;
24 default_type application/octet-stream;
25
26 # logging
27 access_log /var/log/nginx/access.log;
28 error_log /var/log/nginx/error.log warn;
29
30 # SSL
31 ssl_session_timeout 1d;
32 ssl_session_cache shared:SSL:10m;
33 ssl_session_tickets off;
34
35 # Mozilla Intermediate configuration
36 ssl_protocols TLSv1.2 TLSv1.3;
37 ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384;
38
39 # OCSP Stapling
40 ssl_stapling on;
41 ssl_stapling_verify on;
42 resolver 1.1.1.1 1.0.0.1 8.8.8.8 8.8.4.4 208.67.222.222 208.67.220.220 valid=60s;
43 resolver_timeout 2s;
44
45 # load configs
46 include /etc/nginx/conf.d/*.conf;
47
48server {
49 listen 10061;
50 location /nginx_status {
51 stub_status on;
52 access_log off;
53 # allow 127.0.0.1;
54 # deny all;
55 }
56 }
57}
58
59
-
include /etc/nginx/conf.d/*.conf;
-
这只是全局的配置,对于每个域名的配置,以及安全策略、代理之类的配置在/conf.cinclude配置
-
Nginx 开启status用以监控状态信息,看下面的配置:
2
3
4
5
6
7
8
9
10
11
2 listen 10061;
3 location /nginx_status {
4 stub_status on;
5 access_log off;
6 # allow 127.0.0.1;
7 # deny all;
8 }
9 }
10
11
-
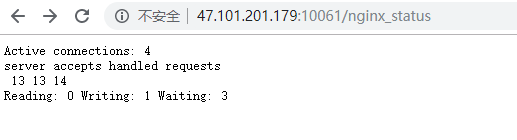
Active connections: 4 表示Nginx正在处理的活动连接数4个。
-
server 13 表示Nginx启动到现在共处理了13个连接
-
accepts 13 表示Nginx启动到现在共成功创建13次握手
-
handled requests 14 表示总共处理了 14 次请求
-
Reading:Nginx 读取到客户端的 Header 信息数
-
Writing:Nginx 返回给客户端 Header 信息数
-
Waiting:Nginx 已经处理完正在等候下一次请求指令的驻留链接(开启keep-alive的情况下,这个值等于Active-(Reading+Writing))
2
3
2
3
-
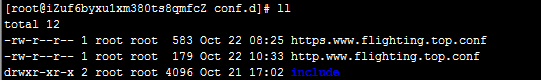
新增****.conf,如图命名规则,可以清晰看出访问方式以及域名
-
https.www.flighting.top.conf
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
2server {
3 # SSL开启方式
4 listen 443 ssl;
5 server_name www.flighting.top;
6
7 # SSL
8 ssl_certificate /etc/nginx/crt/test.crt;
9 ssl_certificate_key /etc/nginx/crt/test.key;
10
11 # security
12 #include conf.d/include/security.conf;
13
14 # logging
15 access_log /var/log/nginx/access.log;
16 error_log /var/log/nginx/error.log warn;
17
18 # reverse proxy
19 #location / {
20 # proxy_pass http://mps;
21 # include conf.d/include/proxy.conf;
22 #}
23 location / {
24 root /usr/share/nginx/html;
25 index index.html index.htm;
26 }
27
28 # additional config
29 #include conf.d/include/general.conf;
30}
31
32
2
3
4
5
6
7
8
9
10
11
12
13
2server {
3 listen 80;
4 server_name www.flighting.top;
5
6 location / {
7 root /usr/share/nginx/html;
8 index index.html index.htm;
9 }
10}
11
12
13
-
ssl_certificate 、ssl_certificate_key 就是crt下面的crt、key文件
-
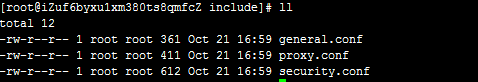
下面来看include下面的几个文件
-
general.conf
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
2location = /favicon.ico {
3 log_not_found off;
4 access_log off;
5}
6
7# robots.txt
8location = /robots.txt {
9 log_not_found off;
10 access_log off;
11}
12
13# gzip
14gzip on;
15gzip_vary on;
16gzip_proxied any;
17gzip_comp_level 6;
18gzip_types text/plain text/css text/xml application/json application/javascript application/rss+xml application/atom+xml image/svg+xml;
19
20
-
proxy.conf
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
2location = /favicon.ico {
3 log_not_found off;
4 access_log off;
5}
6
7# robots.txt
8location = /robots.txt {
9 log_not_found off;
10 access_log off;
11}
12
13# gzip
14gzip on;
15gzip_vary on;
16gzip_proxied any;
17gzip_comp_level 6;
18gzip_types text/plain text/css text/xml application/json application/javascript application/rss+xml application/atom+xml image/svg+xml;
19[root@iZuf6byxu1xm380ts8qmfcZ include]# cat proxy.conf
20proxy_http_version 1.1;
21proxy_cache_bypass $http_upgrade;
22
23proxy_set_header Upgrade $http_upgrade;
24proxy_set_header Connection "upgrade";
25proxy_set_header Host $host;
26proxy_set_header X-Real-IP $remote_addr;
27proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
28proxy_set_header X-Forwarded-Proto $scheme;
29proxy_set_header X-Forwarded-Host $host;
30proxy_set_header X-Forwarded-Port $server_port;
31
32
-
security.conf
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
2#add_header X-Frame-Options "SAMEORIGIN" always;
3#add_header X-XSS-Protection "1; mode=block" always;
4#add_header X-Content-Type-Options "nosniff" always;
5add_header Referrer-Policy "no-referrer-when-downgrade" always;
6#add_header Content-Security-Policy "default-src 'self' http: https: data: blob: 'unsafe-inline'" always;
7#add_header Content-Security-Policy "default-src 'self' http: https: data: blob: 'unsafe-inline' 'unsafe-eval'" always;
8add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
9
10
11# . files
12location ~ /\.(?!well-known) {
13 deny all;
14}
15
16
- 这些只是常用的,具体的看项目需求。
3、测试
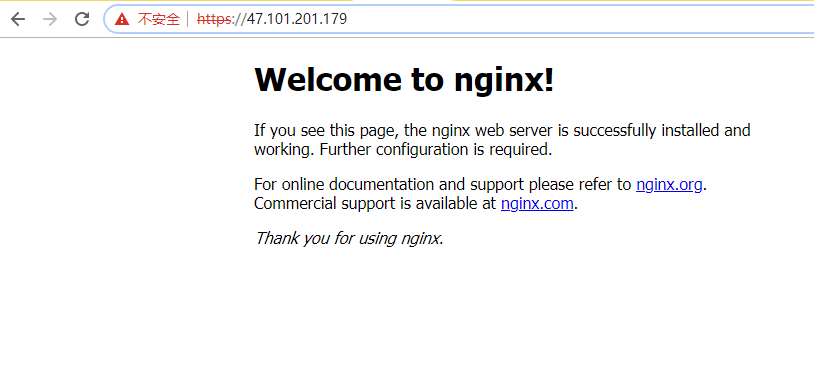
- 由于域名未备案,所以只能访问ip
- 访问https://47.101.201.179,提示不安全的链接
关注公众号"双城人",搬砖过程遇到的问题,大家一起探讨,资源共享

